 By making their IoT platforms symbIoTe enabled, the IoT platform providers can expose their resources to third party applications. Their resources will be searchable through symbIoTe Core Services and able to be used together with resources from other IoT platforms. In such a way platform providers ensure a wider usage of their resources in the IoT ecosystem. This blog post lists the main steps platform providers should perform to make their platforms symbIoTe enabled.
By making their IoT platforms symbIoTe enabled, the IoT platform providers can expose their resources to third party applications. Their resources will be searchable through symbIoTe Core Services and able to be used together with resources from other IoT platforms. In such a way platform providers ensure a wider usage of their resources in the IoT ecosystem. This blog post lists the main steps platform providers should perform to make their platforms symbIoTe enabled.
A Step by Step HowTo
The symbIoTe project is implementing an interoperable mediation framework to enable the discovery and sharing of connected devices across different IoT platforms for rapid development of cross-platform IoT applications. The project focuses on different interoperability aspects, and in this blog we concentrate on achieving semantic interoperability, which we call in symbIoTe Level-1 Compliance.
The main incentive to make platforms symbIoTe enabled comes from the possibility to expose resources to a wider audience, which creates new revenue streams for platform providers/owners. As shown in Figure 1, resources from one IoT platform can be exposed to third-party applications, and used along with resources from other symbIoTe-enabled platforms. To enable such a scenario, resources from different platforms need to be described in line with the Core Information Model (CIM), a minimalistic model defining core IoT concepts, and which can be extended if needed by specifying additional platform-specific concepts.
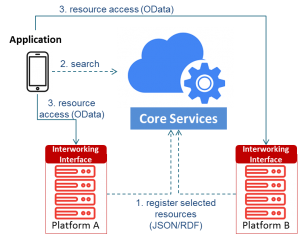
Figure 1 – symbIoTe Semantic Interoperability (Level-1)
The process of making IoT platforms symbIoTe L1 enabled consists of downloading and setting up of symbIoTe Cloud components (shown in red in Figure 2), integrating these components with the platform, and registering the platform and resources to symbIoTe Core Services (shown in blue in Figure 2).
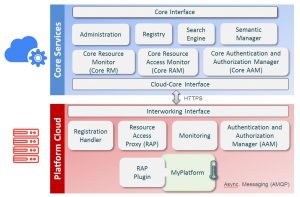
Figure 2 – symbIoTe Level-1 Components
Components in symbIoTe CLD and their main functionalities are the following:
- Registration Handler (RH): handles registration of resources which platform providers want to expose to symbIoTe Core Services,
- Resource Access Proxy (RAP): receives requests for resource access from applications who found resource metadata through symbIoTe Core Services,
- Monitoring: monitors the status of resources, and
- Authentication and Authorization Manager (AAM): enables a common authentication and authorization mechanism for applications.
symbIoTe Core Services are a central point where third-party applications can search for cross-platform resources. IoT platforms register only resource metadata to the symbIoTe Core Services, while resource access requests need to be directed to the corresponding IoT platform.
The steps platform providers should complete to make their IoT platforms symbIoTe enabled are the following:
- Download and configure symbIoTe CLD components,
- Register the resources they would like to share within symbIoTe Core Services,
- Find the resources through symbIoTe Search Engine, and
- Access the resources through symbIoTe CLD.
After performing the aforementioned steps, the platform providers can be sure that their resources are registered in symbIoTe Core Services and able to be accessed by the third-party applications. Step by step guide is given in the following paragraphs. For technical details on the integration you can refer to the project’s GitHub space for symbIoTe Cloud available at https://github.com/symbiote-h2020/SymbioteCloud.
STEP-1. Download and setup of CLD components and required tools
Before installation of the symbIoTe Cloud components, platform providers should install the tools that are a prerequisite for the execution of Cloud components. These tools are:
- Java Development Kit – version 8 with Letsencrypt certificate compatibility,
- RabbitMQ – message queue server for internal messaging between platform components,
- Mongo DB – database used by platform components, and
- Nginx – proxy server serving as Interworking Interface for receiving all the requests directed to symbIoTe CLD, redirects the requests to corresponding platform components.
After the installation of these tools, Nginx will need to be configured so that it redirects all the requests correctly to the corresponding components. The symbIoTe Coud components are implemented as microservices and need to be downloaded from the project’s git repository. Apart from the components introduced in the Figure 2 (Resource Access Proxy, Registration Handler, Monitoring, and Authentication and Authorization Manager, symbIoTe Cloud also contains the following:
- Zipkin service,
- Eureka service, and
- Cloud Config service.
Zipkin service collects logs from various services, while Eureka service allows discovery of platform components. Cloud Config service is responsible for configuration of user credentials, ports and interfaces used in communication between symbIoTe Cloud and symbIoTe Core Services.
After installing the symbIoTe Cloud components, platform providers need to connect symbIoTe Cloud with their platform and enable access to the resources. Afterwards, registration to the symbIoTe Core Services is needed, followed by the generation of security certificates.
STEP-2. Platform-specific plug-in
RAP platform plugin is a part of RAP in charge of accessing the resources exposed by the platform. Platform providers are required to implement the code which can acquire the data from the platform. After obtaining the data, plugin forwards it to the generic part of the RAP which then handles all communication with the upper layers, i.e. the users of the exposed data.
RAP supports:
- acquiring the current value from resource,
- reading history values from resource,
- subscribing to resource values and creating notifications, and
- writing values into resources when dealing with actuating devices.
Corresponding methods are defined within provided platform plugin that needs to be implemented for each IoT platform. After the implementation, platform plugin will be integrated with the generic part of the RAP during build process.
STEP-3. Registering platform to symbIoTe Core
To enable usage of its platform within symbIoTe ecosystem, IoT platform providers need to register to symbIoTe Core Services. For this purpose, symbIoTe Core Admin webpage is available where platform providers are supposed to enclose basic information about their platforms, as shown in Figure 3.
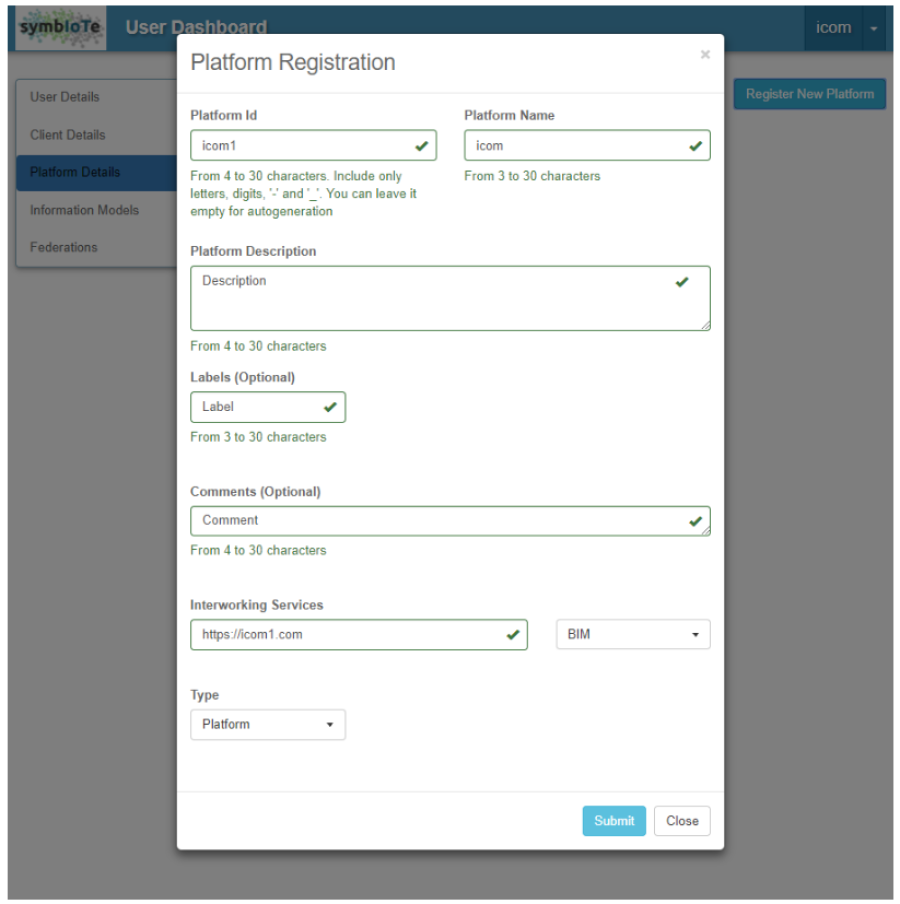
Figure 3 Platform registration
During registration process, platform providers can create their own Platform-Specific Information Model (PIM) allowing them to offer certain descriptions to their resources that aren’t included in Core Information Model.
STEP-4. Platform Authentication and Authorization Manager
The last step in configuration of platform components is setting up the Authentication and Authorization Manager. The platform providers should generate two certificates:
- PAAM certificate, and
- SSL certificate.
PAAM certificate can be generated by using the keystore factory available in symbIoTe Security module. SSL certificate can be generated by using certbot shell tool. After the generation of the certificates, the generated keystore needs to be copied into the corresponding directories.
After the implementation of Platform specific plugin, generation of certificates and configuration of components, the platform provider is ready to build and run all the components.
STEP-5. Registering resources
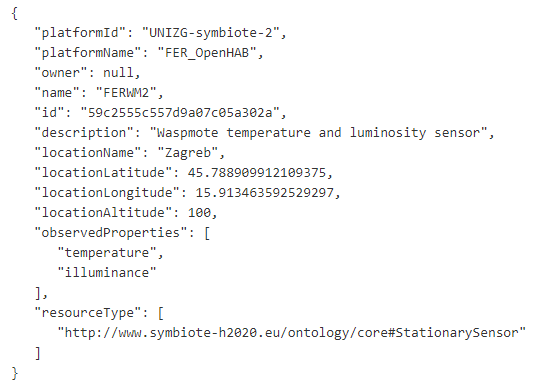
After the setup process has finished, platform providers can register the first resources they would like to expose to symbIoTe Core Services. This is done by sending HTTP post requests to Registration Handler component (e.g. http://myplatform.eu:8102/rh/resources). Resource needs to be described according to Platform-Specific Information Model which extends symbIoTe Core Information Model. The example for a sensing device with connected temperature and luminosity sensors is shown in Figure 4. It is also possible to use RDF (Resource Description Framework) for describing resources. Platform providers also have the possibility to update and delete the resources they expose to symbIoTe Core Services.
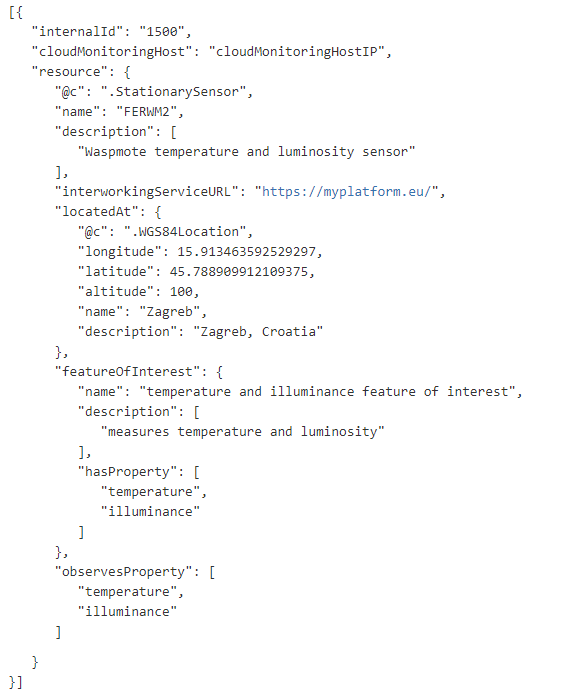
Figure 4 Resource description
After the successful setup of symbIoTe Cloud and registration of first resources, symbIoTe users are able to find and access the resources of the newly registered IoT platform.
Step6. Finding resources through symbIoTe Core
To search for resources, a query needs to be sent to symbIoTe Core (e.g. https://core.symbiote.eu:8100/coreInterface/v1/query?platform_name=FER_OpenHAB).
Users can choose among different query parameters (platform name, description, location, observed property etc.).
The example of the description for the resource previously registered is shown in Figure 5.
After finding the desired resource, users need to access it. As already mentioned earlier, symbIoTe Core Services store only resource metadata. To access the resource values, users need to contact IoT platforms to which resources are connected to.
STEP7. Access to platform resources from third-party applications
Firstly, users need to acquire the access link which is provided after sending HTTP request to symbIoTe Core Services with the id of the resource as input parameter (e.g. https://core.symbiote.eu/coreInterface/v1/resourceUrls?id=59c2555c557d9a07c05a302a). In the response, symbIoTe Core Services provide URL of the resource.
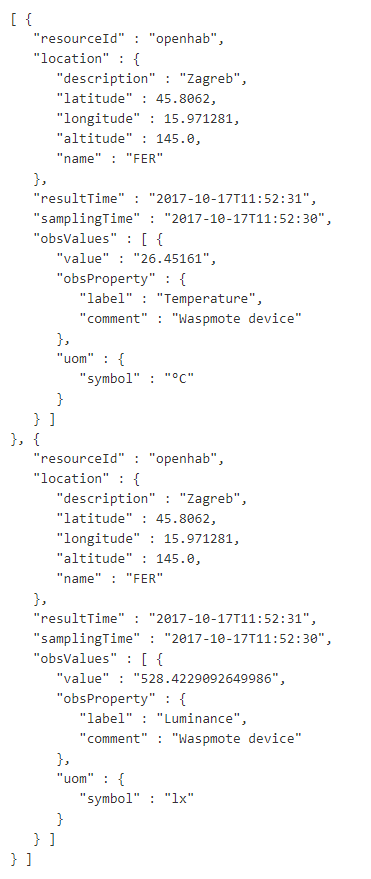
Afterwards, the users can access the resource values (e.g. https://myplatform.eu/rap/Sensor/59c2555c557d9a07c05a302a). Example of the resource value for the resource already presented Figure 4 and Figure 5 is given in Figure 6. In the example it can be seen that the current value of temperature is 26.4 °C, while luminance value is 528 lx.
Conclusions
With this step-by-step howto we’ve showed how it is possible to read of the current value from a resource in symbIoTe. Additionally, RAP can read history values from resource and write values into resource (in the case of actuators). Furthermore, through RAP WebSocket, applications can subscribe to receive notifications from resources. Apart from REST interface that has been used in this example to access the data, OData interface (http://www.odata.org/) can also be used.
We showed the main steps the platform providers need to go through in order to make their IoT platforms symbIoTe enabled.
All the technical details on how to setup symbIoTe Cloud components and how to expose resources can be found on page https://github.com/symbiote-h2020/SymbioteCloud.
Pavle Skocir (UNIZG-FER)


 This project has received funding from the European Union's Horizon 2020 research and innovation programme under grant agreement No 688156
This project has received funding from the European Union's Horizon 2020 research and innovation programme under grant agreement No 688156